
Understanding the diffrence between hot vs cold types of crypto wallets is crucial because, it helps you decide whether convenience or maximum security matters more to you. At the same time knowing how custodial vs non-custodial wallets work gives you the clarity to choose between simplicity and full ownership of your private keys. As the crypto market grows the people who understand these wallet types are the ones who stay safer, make smarter decisions and manage their digital assets with confidence. The world of cryptocurrency is expanding faster than ever before and with this rapid growth comes the increasing need to understand the types of crypto wallets available today. As more people invest, trade and adopt digital assets, choosing the right wallet has become one of the most important decisions in crypto security.
Whether you are a complete beginner just starting your crypto journey or an experienced professional trader managing multiple portfolios learning about the different types of crypto wallets can help you protect your money and avoid costly mistakes. A crypto wallet is a digital tool that safely stores your private keys and the secret codes that prove you own your cryptocurrency and let you send or receive it. Since your private keys give you control over your crypto choosing the right wallet is very important.
Understanding the different types of crypto wallets is helpful because each wallet handles your keys in its own way and offers a mix of convenience, security and control. Some wallets stay connected to the internet at all times making them fast and easy to use. These are known as hot wallets. Others keep keys offline for maximum protection these are cold wallets. Meanwhile wallets also differ by who controls the keys custodial wallets where a company holds your keys and non-custodial wallets where you hold them yourself. [1]
Before selecting any wallet it’s important to understand both classifications clearly:
- Types of crypto wallets based on internet connection: hot vs cold crypto wallets
- Types of crypto wallets based on key ownership: custodial vs non-custodial wallet
Types of Crypto Wallets Based on Internet Connection
The first way to categorize the types of crypto wallets is by checking whether the wallet is connected to the internet. This gives us the popular division: hot vs cold crypto wallets.
Understanding hot vs cold types of crypto wallets helps you choose between convenience and high-level security.
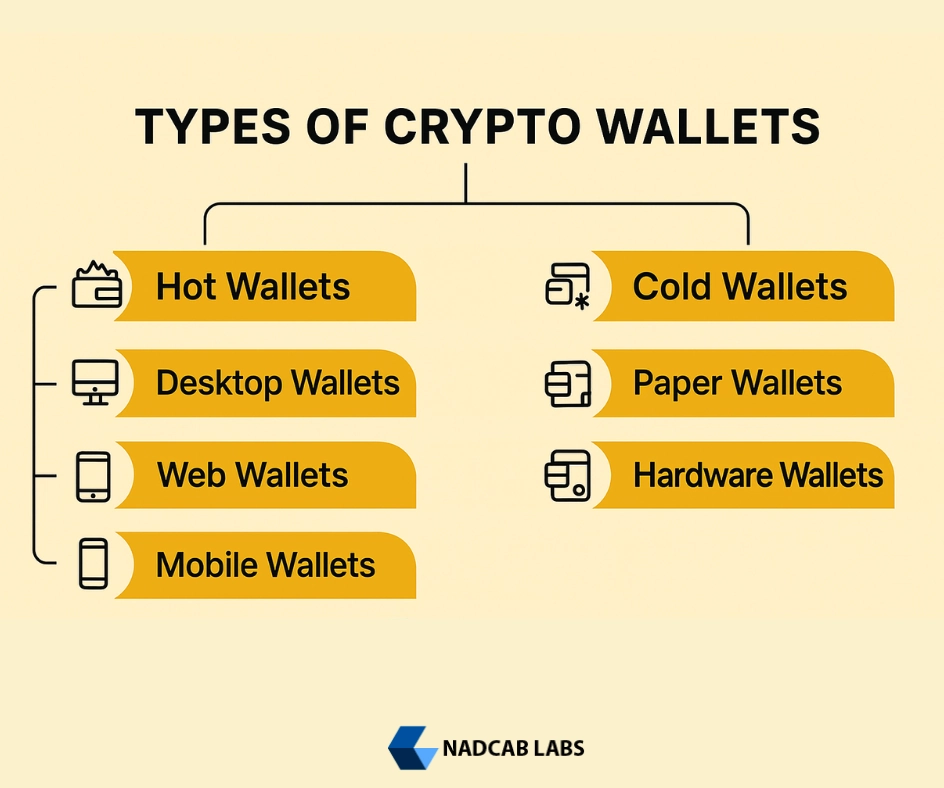
Hot Crypto Wallets (Online Wallets)
Hot wallets are the types of crypto wallets that stay connected to the internet making them fast simple and ideal for everyday use. When exploring the types of crypto wallets hot wallets are usually the first option most beginners come across. They are best for beginners daily crypto transactions frequent trading and interacting with DeFi platforms or NFTs. Popular examples of hot wallets include MetaMask, Trust Wallet, Coinbase Wallet (non-custodial) and exchange-based wallets.
Hot wallets offer easy usage quick access to funds and are great for holding small amounts of cryptocurrency especially for active users. However, they also come with security risks such as hacking, malware infections and device-based threats. Because they remain online they are not recommended for storing large or long-term holdings. When comparing hot vs cold crypto wallets hot wallets clearly provide more convenience but offer less maximum security.
Types of Hot Crypto Wallets
1.Mobile Wallets
Mobile wallets are crypto applications installed on your smartphone allowing you to store, send and receive crypto directly from your mobile device. They are especially popular among beginners because they are simple, intuitive and perfect for everyday use. Mobile wallets are great for QR based payments, quick transactions and checking your balance on the go. Popular examples include Trust Wallet, MetaMask Mobile and the Coinbase Wallet app. Their biggest strengths are convenience accessibility and ease of use. However they also carry risks your funds can be vulnerable if your phone gets infected with malware or if your device is lost or hacked.
2.Desktop Wallets
Desktop wallets are installed on a computer and offer a good balance between usability and security. They are ideal for traders, DeFi users and people who want more control over their crypto. Well-known desktop wallets include Exodus, Electrum and Atomic Wallet. These wallets are more secure than mobile wallets because they operate on a desktop environment but they still face online threats. If your computer gets infected with viruses, keyloggers or malware your funds can be compromised. Even though they provide better features for advanced users they still require responsible device security.
3.Web Wallets (Browser-Based Wallets)
Web wallets work directly through your internet browser or as browser extensions making them one of the easiest ways to interact with Web3 platforms and decentralized applications. They are commonly used by NFT enthusiasts, DeFi users and beginners who prefer quick setup. Popular examples include the MetaMask extension and Coinbase Wallet extension. These wallets are fast, simple and extremely convenient for interacting with blockchain apps. However they are also highly vulnerable to phishing attacks and depend heavily on browser security. This makes safe browsing habits very important.
4.Exchange Wallets
Exchange wallets are provided by centralized exchanges (CEX) making them perfect for beginners who want a simple login experience without dealing with private key management. Examples include the Binance wallet, Coinbase exchange wallet and Kraken wallet. These wallets offer password recovery options, customer support and a very user-friendly interface. However the biggest drawback is that you do not control your private keys the exchange does. This means your assets may be at risk if the exchange is hacked or faces issues. Some platforms may also have withdrawal limits or restrictions.
5.Multi-Signature Hot Wallets (Multi-Sig)
Multi-signature hot wallets require more than one private key to authorize a transaction. This makes them ideal for companies, teams or any high-security environment where multiple approvals are needed. A well-known example is the online version of Gnosis Safe. These wallets provide strong protection by eliminating single points of failure no single person can steal or misuse the funds alone. However this added security comes with complexity. Multi-sig wallets are harder to set up and are not recommended for beginners because they require multiple people or devices to work together.
Cold Crypto Wallets (Offline Wallets)
Cold wallets stay completely offline, storing your private keys without any internet connection which makes them the safest among all types of crypto wallets. They are ideal for long-term holding storing large amounts of crypto and achieving maximum security. Common examples of cold wallets include hardware wallets like Ledger and Trezor, paper wallets and air gapped devices. Cold wallets offer major advantages such as zero online hacking risk full control over your private keys and strong long-term protection for your investments.
However they are less convenient than hot wallets because they require careful backup and hardware devices come with a cost. When comparing hot vs cold crypto wallets, cold wallets are clearly the best choice for long-term storage and maximum safety while hot wallets are better suited for daily usage and active trading.
Types of Cold Crypto Wallets
1. Hardware Wallets
Hardware wallets are physical devices that securely store your private keys offline. They only connect to the internet when you plug them into a computer or mobile device to approve a transaction. Popular models include Ledger Nano S/X and Trezor Model T. These wallets provide extremely strong security because your keys never leave the device. Even if your computer is infected with malware, your private keys remain safe. Their main drawback is cost they are not free and they require proper handling and backup of seed phrases.
2. Paper Wallets
A paper wallet is a simple, offline method where your public and private keys are printed on paper. Since they are completely offline, they offer strong protection against online hacking. However paper wallets require extra care if the paper is damaged, lost or stolen the funds cannot be recovered. They are best for long-term storage but less ideal for beginners due to the risk of physical loss or damage.
3. Air-Gapped Wallets or Devices
Air-gapped wallets are devices that never connect to the internet, Wi-Fi, Bluetooth or any wireless network. These can be old laptops, computers or specialized crypto devices that are permanently offline. Transactions are created offline and signed using QR codes or USB transfers. This provides ultra-high security and is often used by institutions or high-net-worth investors. The downside is complexity air-gapped wallets require more technical knowledge and are not practical for everyday users.
4. Cold Multi-Signature Wallets
Cold multi-sig wallets combine the power of offline storage with multi-signature security. This means multiple approvals are required to release funds, even though all keys are stored offline. This setup is excellent for large organizations partnerships or secure treasury management. While extremely secure it can be difficult to set up and requires coordination among multiple parties making it less suitable for beginners.
5. Offline Desktop or Offline Mobile Wallets
Some users create cold wallets by installing wallet apps on devices that never connect to the internet. These offline only devices act like miniature vaults. Since they never go online they cannot be hacked remotely. However they require advanced technical understanding and careful management of backups to avoid permanent loss of access.
Types of Crypto Wallets Based on Ownership
The second way to understand the types of crypto wallets is to check who controls the private keys. This gives us custodial vs non-custodial wallets.

This category is essential for security and true ownership.
Custodial Wallets
Custodial wallets are the types of crypto wallets where a third-party company controls your private keys meaning you rely on the service provider to manage and secure your funds. When learning about custodial vs non-custodial wallets custodial options are usually recommended for beginners because they offer a simple and user-friendly experience. Popular examples include the Binance exchange wallet, Coinbase exchange wallet and the Kraken wallet.
These wallets come with several advantages such as easy login password recovery options and dedicated customer support. However they also have important drawbacks you don’t fully own your private keys exchange hacks can lead to losses and some platforms may impose withdrawal limits. In the comparison of custodial vs non-custodial wallets custodial wallets are definitely the easiest to use but not the safest option for those who want complete control over their crypto assets.
Non-Custodial Wallets
Non-custodial wallets give you complete control over your private keys which means you truly own your crypto without depending on any third party. When exploring the types of crypto wallets non-custodial wallets are often considered the purest form of crypto ownership. Popular examples include MetaMask, Trust Wallet, hardware wallets and Electrum. These wallets offer major advantages such as full ownership of your assets, protection from company freezes and stronger privacy. However they also come with responsibilities if you lose your seed phrase your funds cannot be recovered, and there is no customer support to rely on. In the discussion of custodial vs non-custodial wallets, non-custodial wallets provide better security and freedom but require careful handling and self-discipline.
Comparison Table Hot vs Cold vs Custodial vs Non-Custodial
Below is a simple and clear comparison table to help readers understand the main differences among all types of crypto wallets:
| Types of crypto wallets | Internet Connection | Who Controls the Keys? | Best For | Security Level | Examples |
|---|---|---|---|---|---|
| Hot Wallets | Online | User | Daily transactions, beginners, trading | Moderate | MetaMask, Trust Wallet, Coinbase Wallet |
| Cold Wallets | Offline | User | Long-term holding, storing large amounts | Very High | Ledger, Trezor, Paper Wallets |
| Custodial Wallets | Online or Offline | Third-party company | Beginners wanting simple login & recovery | Depends on provider | Binance Wallet, Coinbase Exchange Wallet, Kraken |
| Non-Custodial Wallets | Online or Offline | User | Full ownership, privacy, DeFi | High (if managed properly) | MetaMask, Hardware Wallets, Electrum |
This comparison helps you clearly understand hot vs cold crypto wallets and custodial vs non-custodial wallets making it easier to choose the right one based on convenience security and control.
How Crypto Wallets Actually Work
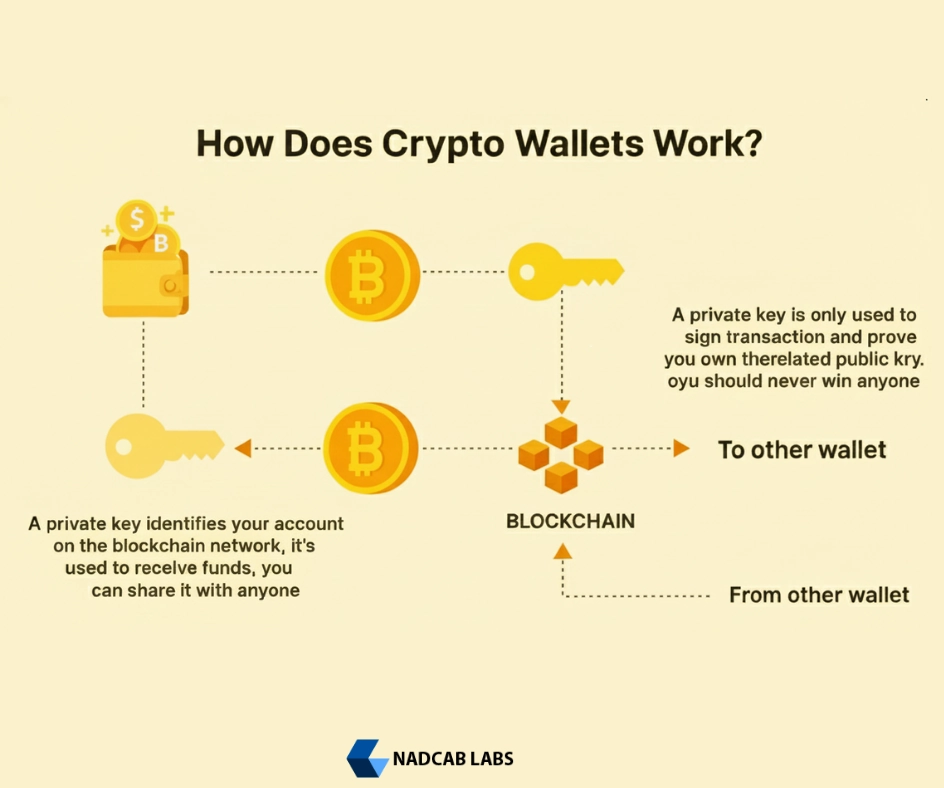
Crypto wallets do not actually store your cryptocurrency inside the wallet itself. Instead they store your private keys which are the digital passwords that prove your ownership of crypto stored on the blockchain. When you send crypto your wallet uses your private key to “sign” the transaction and broadcast it to the blockchain network. When you receive crypto, the blockchain records it under your public address and your wallet simply allows you to view and control your funds.
Every types of crypto wallets whether hot or cold custodial or non-custodial works on the same fundamental principle it stores and protects your private keys which are the digital credentials required to access and authorize transactions for your holdings on the blockchain. A hot wallet keeps your keys online for quick access and easy transactions while a cold wallet stores them offline for maximum protection against online threats. In terms of control a custodial wallet entrusts your private keys to a third-party service (like an exchange) whereas a non-custodial wallet gives you exclusive control only if you hold the keys and can authorize transactions.
Crypto wallets do not hold your coins or tokens the actual assets remain on the blockchain and the wallet only manages the keys that unlock your access. If you lose your private keys you lose access to your funds[2].
Build My Crypto wallet Now!
Turn your dream into reality with a powerful, secure crypto wallet built just for you. Start building now and watch your idea come alive!
Security Tips for All Wallet Types
No matter which option you choose among the types of crypto wallets it’s important to follow strong security practices to protect your digital assets. Always keep your seed phrase private and never store it digitally as anyone who gains access to it can instantly take control of your funds. For large amounts of crypto Hardware wallets or cold wallets provide an additional layer of security for storing digital assets.
Make sure to keep secure backups of your seed phrase in safe separate locations to ensure recovery even if one backup is lost or damaged . Before sending any transaction always double-check the entire wallet address because clipboard-poisoning malware has been known to replace copied addresses with fraudulent ones. Enable two-factor authentication on all supported wallets and exchanges for an extra security layer and avoid using public Wi-Fi while accessing your wallet to prevent interception attacks. These simple yet powerful security habits apply to all wallet types whether you’re comparing hot vs cold wallets or choosing between custodial and non-custodial wallets.
Frequently Asked Questions
The main types of crypto wallets are hot wallets, cold wallets, custodial wallets and non-custodial wallets. Hot wallets stay online for easy access while cold wallets remain offline for higher security. Custodial wallets store your keys for you and non-custodial wallets give you full control of your crypto.
The difference between hot vs cold crypto wallets is that hot wallets are online and convenient, while cold wallets are offline and more secure. Hot wallets are great for daily use, trading and DeFi while cold wallets protect large amounts from hacks by keeping private keys offline.
The comparison of custodial vs non-custodial wallets depends on who controls the keys. Custodial wallets store your private keys on your behalf offering easy recovery. Non-custodial wallets give you full control and ownership but require responsible handling of your seed phrase to prevent permanent loss.
In the debate of hot vs cold crypto wallets, cold wallets are safer because they store keys offline, which prevents online hacking. Hot wallets are more convenient but face more security risks. For long-term storage and large amounts, cold wallets offer superior protection compared to hot wallet solutions.
For security and ownership non-custodial vs custodial wallets depend on user responsibility. Non-custodial wallets are safer because you control your keys but losing your seed phrase can cause permanent loss. Custodial wallets are easier for beginners but depend on the company’s security and trustworthiness.
Yes combining hot vs cold crypto wallets is one of the best strategies. Use a hot wallet for daily transactions and trading and use a cold wallet for long-term storage and large amounts. This combination gives you convenience, speed, and maximum protection against hackers and cyber threats.
Absolutely. Many users mix custodial vs non-custodial wallets based on their needs. Custodial wallets are great for beginners, easy buying and quick trading. Non-custodial wallets provide full control for long-term storage. Using both types ensures easy access while maintaining strong ownership and security of your crypto funds.
Beginners should start with hot custodial wallets for easy access, then learn non-custodial options later. Among the types of crypto wallets, custodial hot wallets are simplest but non-custodial hot wallets allow true ownership. Over time beginners should upgrade to cold wallets for safer long-term storage.
No it is safer to split funds across multiple types of crypto wallets. Use hot wallets for daily activity cold wallets for long-term security and decide between custodial vs non-custodial wallets based on convenience or ownership. Diversifying wallets reduces the risk of losing all funds at once.
Losing your seed phrase in non-custodial wallets means you lose access to your crypto forever. This is why seed security matters. In custodial vs non-custodial wallets, custodial wallets allow recovery through support but non-custodial wallets depend only on your backup. Protect your seed with multiple safe copies.
Reviewed By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.




